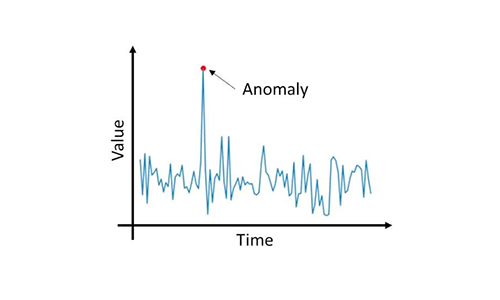
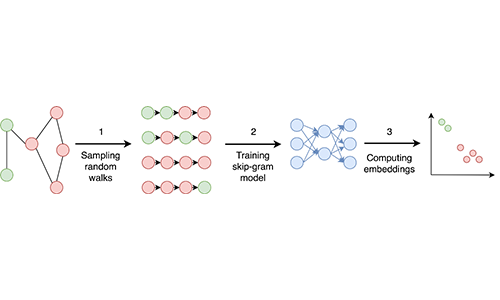
Recommender Systems
A recommender system, or a recommendation system, is a subclass of information filtering system that seeks to predict the "rating" or "preference" a user would give to an item. They are primarily used in commercial applications. Recommender systems are utilized in a variety of areas and are most commonly recognized as playlist generators for video and music services like Netflix, YouTube and Spotify, product recommenders for services such as Amazon, or content recommenders for social media platforms such as Facebook and Twitter. These systems can operate using a single input, like music, or multiple inputs within and across platforms like news, books, and search queries. There are also popular recommender systems for specific topics like restaurants and online dating. Recommender systems have also been developed to explore research articles and experts, collaborators, and financial services.
7) Smart Grid Optimization
With urging problem of energy and pollution, smart grid is becoming ever important. By gradually changing the actual power grid system, smart grid may evolve into different systems by means of size, elements and strategies, but its fundamental requirements and objectives will not change such as optimizing production, transmission and consumption. Studying the smart grid through modeling and simulation provides us with valuable results which can not be obtained in real world due to time and cost related constraints. However, due to the complexity of the smart grid, achieving optimization is not an easy task, even using computer models. Using approaches in game theory and classification methods the optimization may be achieved with flexibility and scalability.